Minecraft players have been exposed to scams and aggressive ads brought by 87 fake Minecraft mods recently spotted on Google Play.
The apps can be divided into two categories – the ad-displaying downloader detected by ESET as Android/TrojanDownloader.Agent.JL and fake apps redirecting users to scam websites, detected as Android/FakeApp.FG.
Altogether, the 87 fake mods reached up to 990,000 installs before we reported them on March 16th and 21st.
Ad-displaying downloader
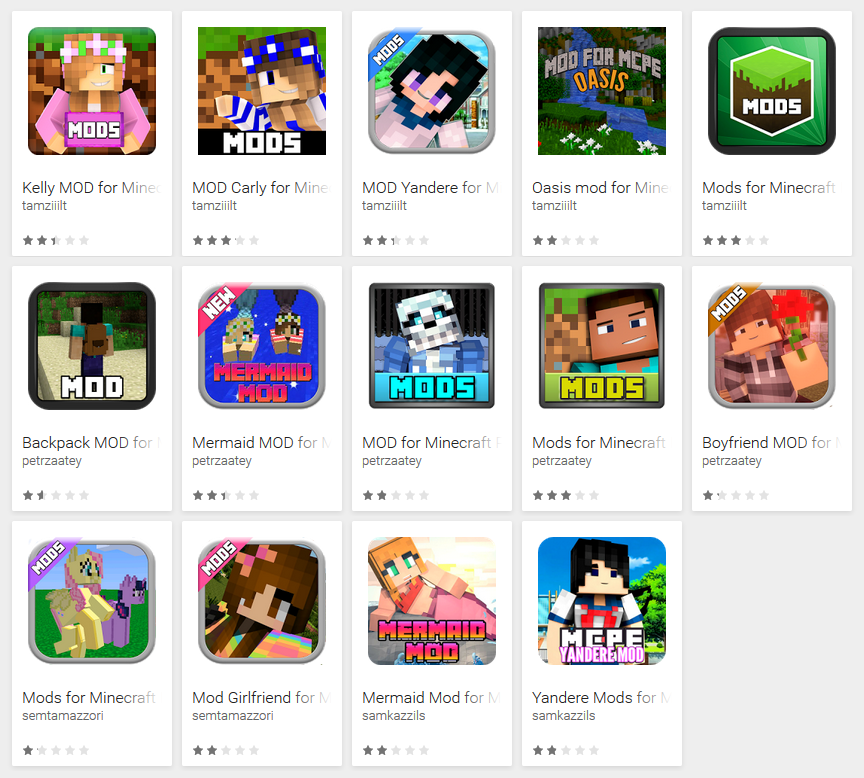
Figure 1 – Ad-displaying downloader disguised as Minecraft mods on Google Play
In the first category, 14 apps impersonating Minecraft mods with up to 80,000 installs have been discovered. Similar to the ad-displaying dropper we analyzed earlier in March, this trojan uses an additional component to display out-of-app advertisements.
In this case, the component acts like a module necessary for installing the mods. The module isn’t a part of the original app – it has to be downloaded from the web and manually installed by the user after launch.
Having no real functionality and displaying aggressive ads, the apps aren’t very popular among users – as shown in the poor ratings and widely negative reviews on Google Play.

Figure 2 – Poor app rating on Google Play
How does it operate?
When launched, the apps immediately request device administrator rights. Once device administrator is activated, a screen with an “INSTALL MOD” button is displayed. Simultaneously, a push notification informs the user that a “special Block Launcher” is needed in order to proceed with the installation.
After clicking the “INSTALL MOD” button, the user is prompted to install the additional module “Block Launcher Pro”, granting it several intrusive permissions (including device administrator rights) in the process. The payload downloaded during the installation is detected by ESET as Android/Hiddad.DA.
Installing the module brings the user to a dead end – a static Minecraft-themed screen with no clickable elements. The only actual function of the app and its module is to display ads – which now show up on the user’s device, interrupting their activity.

Figure 3 – Out-of-app advertisements showing up on victim’s device
Interestingly, this ad-displaying downloader is an evolved version of an app that was originally uploaded to Google Play in February. The original version used a similar interface and also demanded device administrator rights. However, it didn’t have any downloading functionality and, unlike the downloader analyzed in this article, the first version actually provided the user with real Minecraft mods.
Since the result of this evolution – a downloader – is able to download any sort of additional malware to the victim’s device, there is no reason to believe malware authors would stop at only displaying unwanted ads. Seeing they can lure thousands of users into installing their deceptive applications, more dangerous threats distributed under similar disguise might be the next logical step.
Video capture from installation
Fake apps redirecting to scams
The remaining 73 of the detected applications use an old trick of redirecting users to scammy websites. The apps, detected by ESET as Android/FakeApp.FG, were added to Google Play between January and March 2017 and reached up to 910,000 installs before we reported them.

Figure 4 – Scam apps disguised as Minecraft mods on Google Play (click to view all 73 icons)
How does it operate?
Once launched, the apps display a screen with a download button. Clicking the button doesn’t download any mods; instead, it redirects the user to a website opened in a browser. The websites display all kinds of obtrusive content – ranging from ads, through surveys, free coupon offers, jackpot wins, porn, to fake updates and fake virus warnings attempting to scare the user. The messages are displayed to users in different languages based on their IP addresses.

Figure 5 – Fake download screen displayed after launch

Figure 6 – Scam messages displayed upon clicking the download button

Figure 7 – Localized scam messages
How to protect yourself?
If you like to download mods for Minecraft, you might have come across one of these malicious fakes.
With the fake apps redirecting to scam websites, the effects are easy to recognize – the apps don’t work and you’ll see a random scam message upon clicking their fake download button.
In the case of the ad-displaying downloader, there is no functionality either and your device keeps displaying unwanted ads. However, as the downloader is capable of downloading any additional apps to infected devices, the payload responsible for the ads may be substituted by more dangerous malware in the future.
To make sure your device is malware-free, use a reputable mobile security solution to detect and remove the threats.
If you want to remove the threats manually, you can do so by following the steps below.
To clean your device of the ad-displaying downloader, you’ll first have to deactivate device administrator rights for both the app and the downloaded module found under Settings -> Security -> Device administrators, as shown in Fig. 8. Then you can uninstall the apps by going to Settings -> Application Manager.

Figure 8 – Downloaders and payload under active Device administrators

Figure 9 – Downloaders and payload in Application manager
With the scam app, uninstalling is one step easier – you can uninstall the app in Settings -> Application Manager.
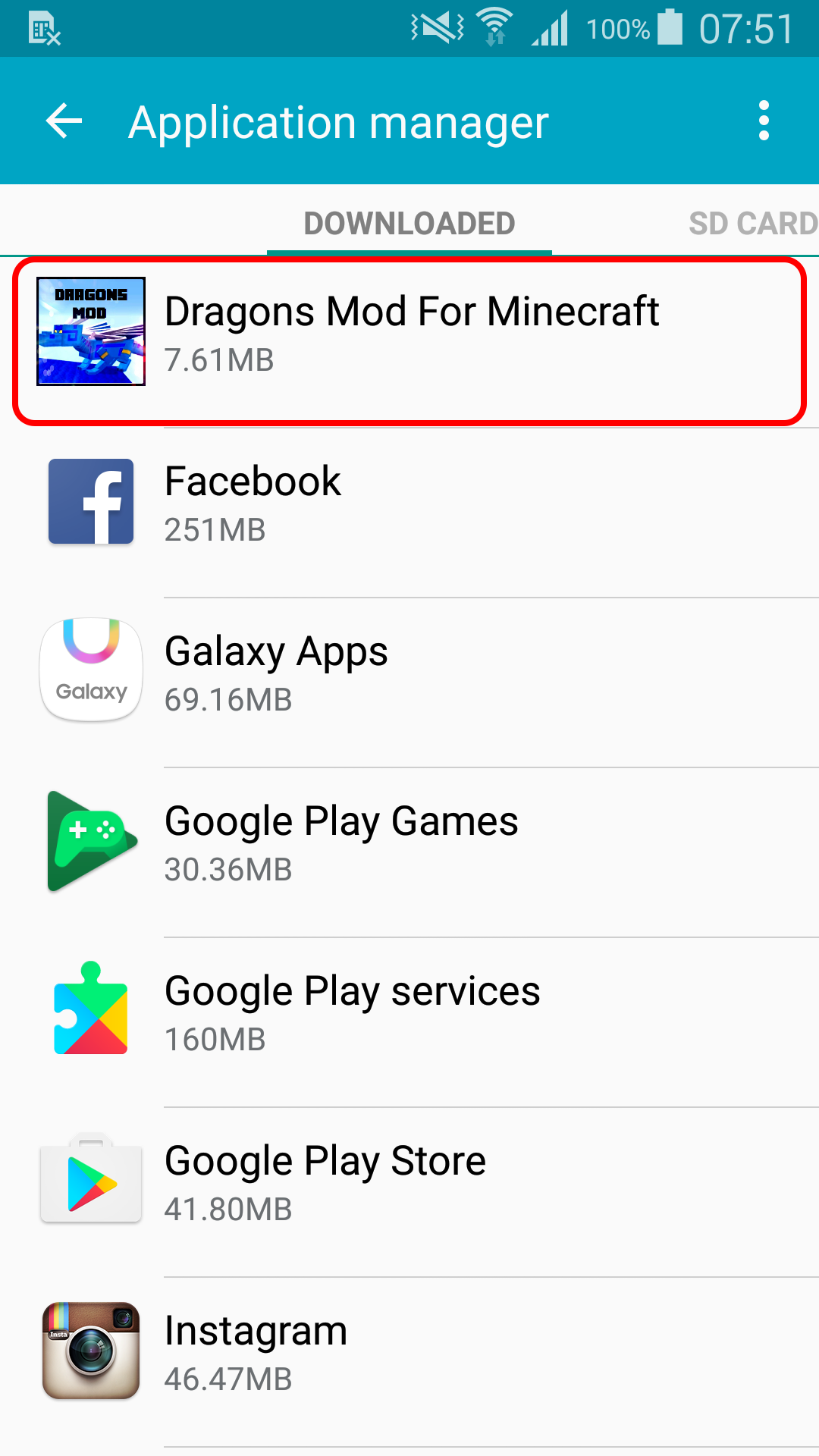
Figure 10 – Fake app in Application manager
To prevent being tricked by fake apps and malware, opt for official app markets. Even then, exercise extra caution when downloading third-party apps offering additional functions to existing applications, as there may be a “catch” in these attractive-sounding offers.
Before downloading, check the popularity of the app by number of installs, ratings and, most importantly, content of reviews. In the case of these apps, low ratings and angry reviews should have been a good enough indicator of their untrustworthiness.
Source: WeLiveSecurity





Share Article