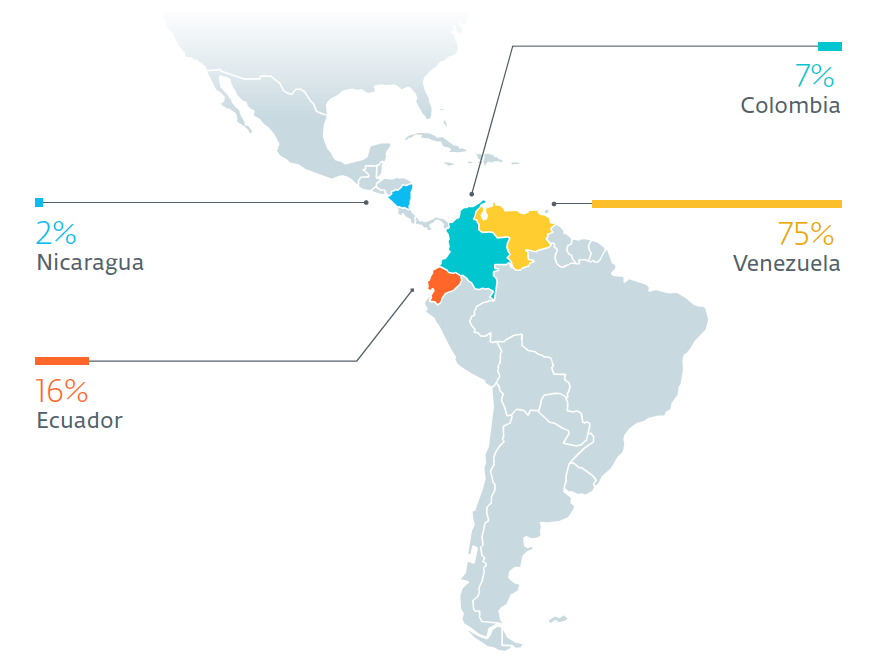
ESET researchers have discovered an ongoing cyberespionage campaign against high-profile targets in Latin America. More than half of the attacked computers belong to Venezuelan military forces. However, among the included targets are institutions ranging from police and education, to foreign affairs. The majority – 75% of the attacks – have taken place in Venezuela, with another 16% taking place in Ecuador, where the military has been a target. The Machete group behind these attacks has stolen gigabytes of confidential documents every single week. The campaign is still very active, and it comes at a time of heightened regional tensions as well as international tensions between the United States and Venezuela.
ESET researchers have been tracking a new version of Machete (the group’s toolset) that was first seen a year ago. Within just three months, between March and May 2019, ESET observed more than 50 victimized computers communicating with Command & Control servers belonging to cyber spies. The attackers are regularly introducing changes to the malware, its infrastructure and spear phishing campaigns.
“Machete’s operators use effective spear phishing techniques. Their long run of attacks, focused on Latin American countries, has allowed them to collect intelligence and refine their tactics over the years. They know their targets, how to blend into regular communications, and which documents are of the most value to steal,” says ESET Researcher Matias Porolli. “The attackers exfiltrate specialized file types used by geographic information systems (GIS) software. The group is specifically interested in files that describe navigation routes and positioning using military grids,” he adds.
Countries with Machete victims in 2019 according to ESET Research
The Machete group sends very specific emails directly to its victims, and these change from target to target. To trick unsuspecting targets, Machete operators use real documents they have previously stolen – for example, classified military documents. Among those are “Radiogramas” (Radiographs), documents used for communication within the military. Attackers take advantage of that, along with their knowledge of military jargon and etiquette, to craft very convincing phishing emails.
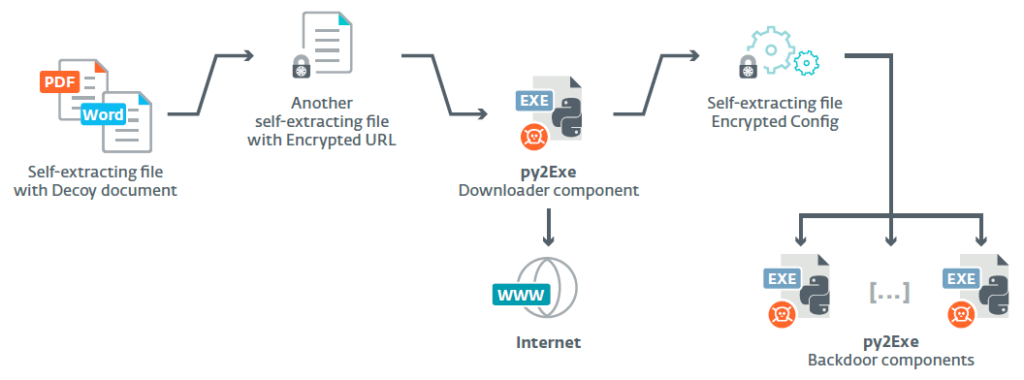
The attack starts with a self-extracting file containing a decoy document, and continues with the downloading and installation of backdoor components. The backdoor consists of a spy component that runs indefinitely, copies and encrypts documents, takes screenshots and records keylogs. The persistence component runs every 30 minutes and installs other components. Also, communication with attackers is secured every ten minutes, in order to send stolen data to the Command & Control server. All the components misuse “Google” in their file names to mask their malicious intent.
“The Machete group’s operations are stronger than ever, and our investigation has shown that it is able to evolve quite rapidly, sometimes within weeks. Different artifacts that we have seen in Machete’s code, and the underlying infrastructure, lead us to think that this is a Spanish-speaking group,” elaborates Matias Porolli from ESET.
Components of Machete according to ESET Research
For more details, read the blogpost, “Machete just got sharper…” and the white paper, “Machete just got sharper: Venezuela’s military under attack” on WeLiveSecurity blog. Make sure to follow ESET research on Twitter for the latest news from ESET Research.






Share Article