Imagine a situation where your Android mobile phone or tablet unexpectedly starts talking to you. A super cool new feature, right? Sure, but only until you realize that the female voice that has just “congratulated” you is actually delivering a message on behalf of lockscreen ransomware. And, if you speak Chinese, you’ve worked out that the price tag for unlocking your Android is set to 40 Yuan (roughly $6).
One member of the well-known Jisut ransomware family (more specifically Android/LockScreen.Jisut) has recently demonstrated these”linguistic skills”. ESET mostly detects the malware as Android/Lockerpin, with regard to its other distinctive feature – the ability to reset the protective lock-screen PIN code.
This talking Android ransomware spreads via a malicious dropper used to decrypt and run the payload. The infection process is activated after the user manually opens the malicious app and taps the “Click for free activation” button at the bottom of the displayed picture.
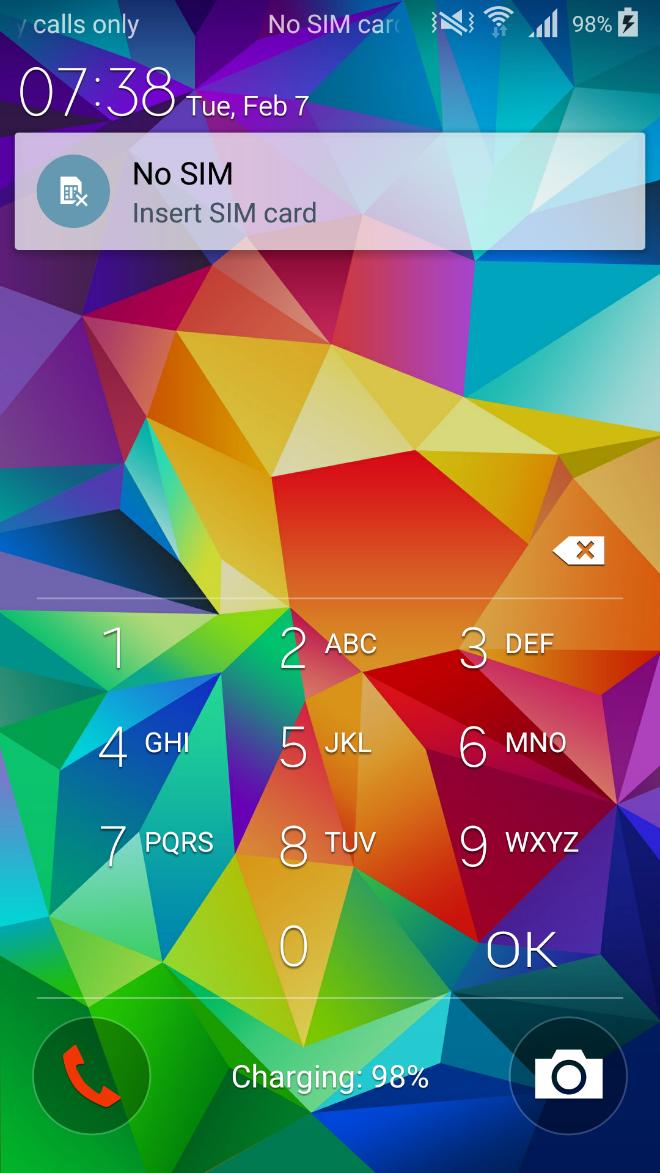
Figure 1 Talking Jisut mimics Lockerpin, changing the original PIN code of the infected device to lock the user out
Subsequently, the victim is asked to grant admin rights to the malware, making it difficult to remove or uninstall the app. On top of that, the device is locked down and the ransom voice message played.
In addition to extortion, the talking Jisut variant has other intentions – one example being its attempt to elicit users’ credentials for the Chinese social network QQ.
The malware attempts to dupe users by displaying a fake login screen, similar to the original one used by the service. Any username or password entered by the user is sent directly to the attacker.
This activity is followed by a ransom demand and information on how to proceed with the payment appears on the user’s screen. There’s no way out: if the user somehow manages to close the activity, it only makes matters worse. The device’s own security feature – PIN lock – is reset to a new entry code, one unknown to the victim.
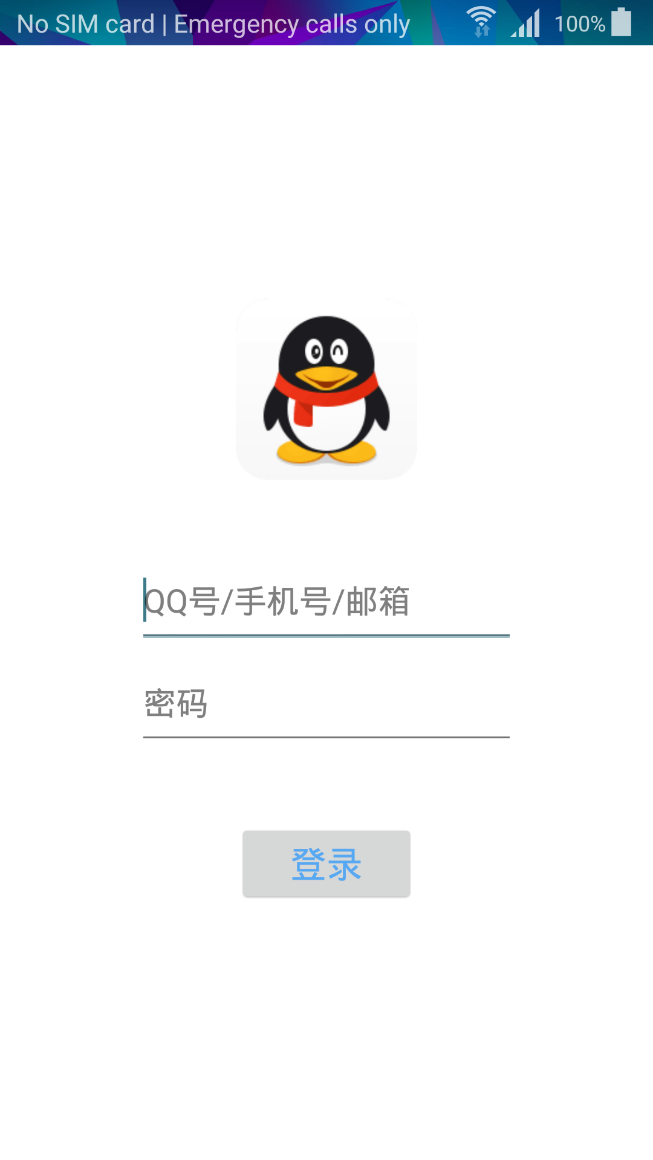
Figure 2 – Fake QQ login screen, trying to elicit the user’s credentials

Figure 3 – Lock-screen with ransom demand
Talking lock-screen is merely one of the new Jisut malware family variants seen over the past year, with the overall number of detections seen by ESET doubling compared to 2015. However, not all of those detected were extorting victims. In fact, some were just trying to sell the app or its source code, or instead, simply locked the device without demanding any ransom.
Variants that asked for money often made the process of paying the ransom simpler and more straightforward by adding a QR code that allowed the user to either send a message to the attacker or to make a direct payment.
The majority of Jisuts had only a visible effect– changing the device’s wallpaper, or audible activity – playing a sound in the background. This reinforces our previously published belief it wasn’t created for purely financial reasons, but also as a prank.
Jisut family is most widespread in China and it is most probably the work of a gang, one that doesn’t care much about anonymity. Some of the past ransomware nag screens included contact information at the Chinese social network QQ and urged victims to contact the authors to get their files back. If the information at QQ is valid, these malware operators are youths between 17 and 22 years old.
The first variants of Android/LockScreen.Jisut started appearing in the first half of 2014. Since then, we have detected hundreds of variants displaying different ransom messages, however all based on the same code template. In addition to the ransomware aspect, some variants are spread via an SMS message with a URL link to the malware to all of the user’s contacts.
To find out more about ransomware on Android, its current trends and most noteworthy examples since 2014, read the newly released whitepaper by ESET. You’re also welcome to stop by at ESET booth B05, in hall 5, at this year’s Mobile World Congress held in Barcelona, February 27th – March 2nd, 2017.
How to get rid of Android/Lockscreen.Jisut
There are three ways to get rid of the malware if your device has been infected:
- You can access it via your mobile device management and manually revoke the admin rights, making it possible to uninstall the infected app. However, there’s a catch: you need to have such an app or functionality installed on the device before being hit by malware.
- If the Android device has been rooted, you can use the Android Debug Bridge option, making it possible to communicate with the smartphone or tablet via command-line. However, this option is limited to experienced Android users or developers.
- The last resort: a factory reset, which returns the mobile device to a fully functional state, but also deletes its content – such as pictures, videos or contacts.
Video Player





Share Article