Ryuk is a ransomware family that has become, unfortunately, only too well known for taking down a library system, medical centers, newspapers, schools, and multiple other institutions and businesses. Within ESET telemetry, Ryuk first appeared as a little seen threat in 2018, one which rose to greater prominence only toward the end of 2019.
Going back to the beginning, the life of the Ryuk ransomware family began in August 2018, at which time ESET dubbed the malware “Win32/Filecoder.NRY.” Detections of this ransomware strain in ESET telemetry* briefly peaked in November 2018, but overall the detections remained low:
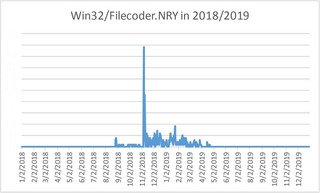
Other researchers in the security community had also noticed this malware early on – Ryuk was starting to gain a bad reputation after hitting at least five businesses within the first month of its arrival.
One peculiar characteristic of Ryuk is that anyone taking a first look at it could be easily misled into mistaking it for the Hermes ransomware family. After all, files encrypted by Ryuk contain – even to this day – the string “HERMES” in the footer. Ryuk, however, is a separate family of ransomware that shouldn’t be confused with Hermes.
At the end of April 2019, ESET renamed this malware “Win32/Filecoder.Ryuk”. The detections with this new name pick up the baton from where detections of “Win32/Filecoder.NRY” leave off:
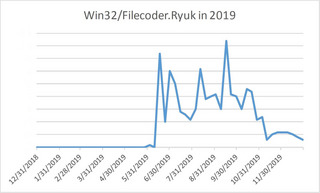
While the detection trend picked up slightly from May 2019, a much greater threat lay in a different form of Ryuk. Ryuk seems to have been recompiled as a new 64-bit version called by ESET “Win64/Filecoder.Ryuk”. Born in March 2019, this new version of Ryuk slowly climbed to a high point in number of detections by September 2019:
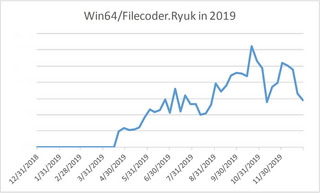
The 64-bit Ryuk targeted about seven times more users at its zenith compared to its 32-bit sibling. Since the time of its birth, the growth of “Win64/Filecoder.Ryuk” occurred quite gradually. Could this gradual growth indicate that the threat actors behind Ryuk were focusing on higher value targets such as businesses or other large organizations rather than home users? The known targeting of Ryuk from the headlines, including such companies as Virtual Care Provider, the National Veterinary Associates and CloudJumper, suggests as much.
Detections of both Ryuk versions throughout 2019 were highest in the United States:
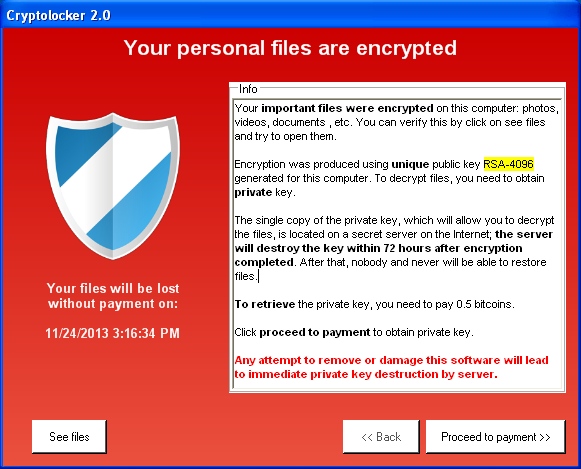
Decrypting Ryuk ransomware?
Ryuk takes advantage of the native CryptoAPI built into Windows operating systems to generate a unique AES-256 encryption key per file. Since AES is a symmetric encryption cipher, a victim will need access to each and every key for successful decryption of all files.
Getting those file keys, however, is unfeasible. The file keys are themselves encrypted by an RSA public key – without any significant implementation flaws – that the Ryuk writers have packaged into the malware executable. RSA is an asymmetric encryption cipher that uses a public-private key pair – whatever is encrypted by the public key can only be decrypted by the private key. That means only the attackers who have the RSA private key can decrypt and give access to the file keys of a victim.
How to stop ransomware attacks
For businesses, there are a number of options specific to ransomware that can help protect against an attack. One crucial check is to make sure that all security solutions deployed in your network are correctly configured.
For example, ESET Endpoint Security, ESET Endpoint Antivirus, ESET Mail Security for Microsoft Exchange and ESET File Security for Microsoft Windows Server all come with a configurable security layer called ESET Host-based intrusion prevention system (HIPS). The HIPS monitors system activity and uses a set of predefined rules to identify and prevent suspicious behavior from running.
IT administrators can further take advantage of HIPS capabilities by deploying tighter configuration settings against ransomware-like behavior on endpoints. Following the anti-ransomware guidelines in the ESET Knowledgebase, admins can add custom rules to prevent specific script executables, Microsoft Office processes and other common processes – like explorer.exe, rundll32.exe and powershell.exe – from launching specific applications or processes not typically required by certain employee profiles.
Unless there is a good business reason (e.g., for employees who are developers), not all employees need to run every kind of script or executable on their devices. These kinds of “don’t need extra scripts/executables” employees can be quickly grouped in ESET Security Management Center, ESET’s remote management tool, for tighter policy management of their HIPS modules.
IT admins can also apply similar anti-ransomware rules within the firewall and antispam modules of ESET endpoint products.
For further information on how to protect your company against ransomware and similar attacks, please see these useful resources:




Share Article